Author: John Higginbotham
Virtualization plays a crucial role in enhancing system security in various ways. I use it to containerize…
As I sit down to write about my love for history, I’m filled with an overwhelming sense…
Data breaches are a seemingly constant occurrence. The frequency of these events has increased dramatically in recent…
My head spins with the things you can do and that are possible with AI… of course…
Data breaches are a seemingly constant occurrence. The frequency of these events has increased dramatically in recent…
I know it’s morbid, but do you ever wonder what the world will be like when you…
Have you heard of domain hijacking? If not, don’t feel left behind. A lot of Internet users…
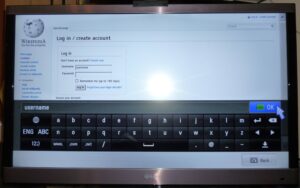
I recently bought a smart tv for my office. I don’t all the time, but occasionally I…